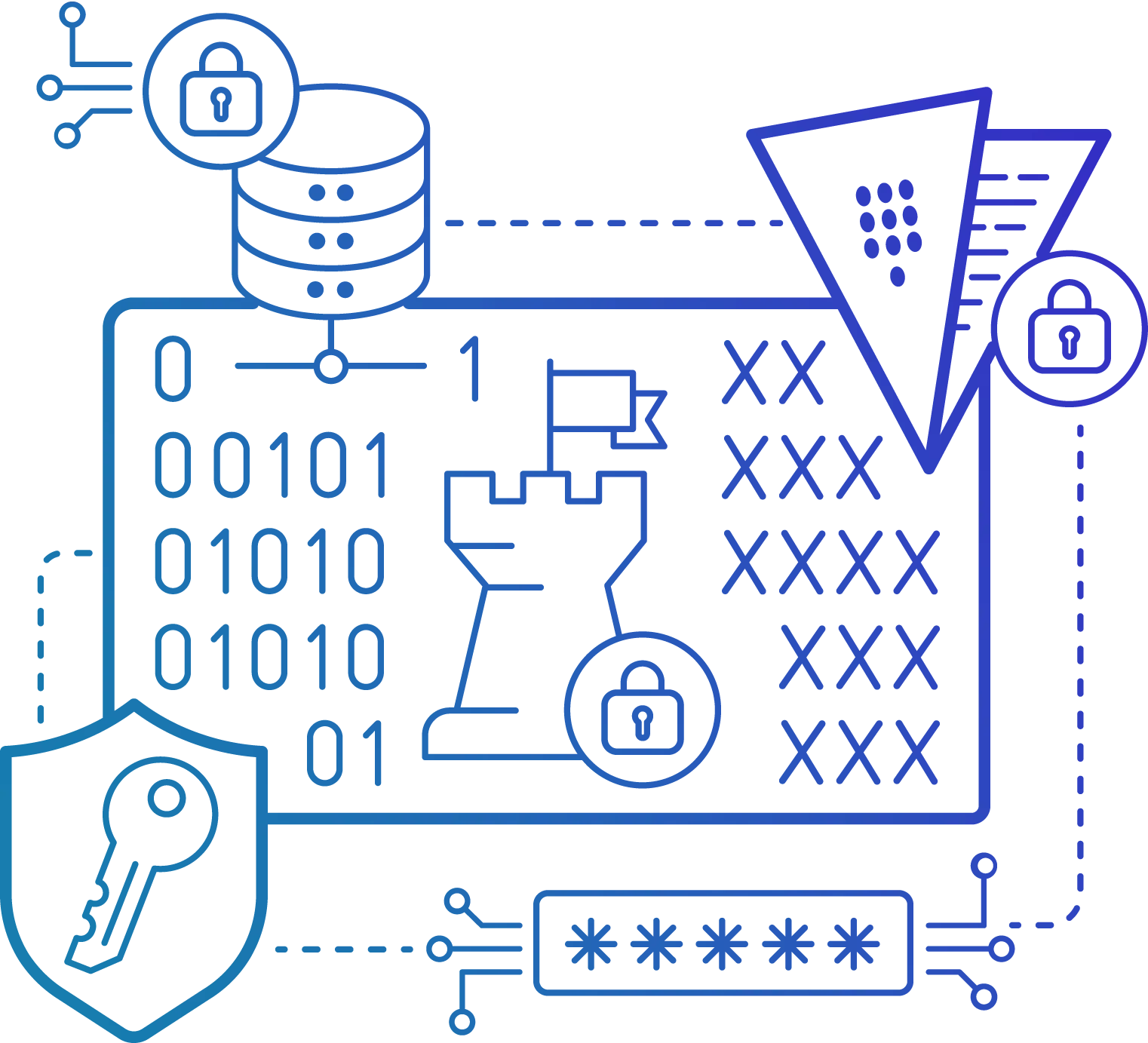
Security
Encryption
Encrypt BlackHark Component-to-Component Communication
![]()
Any communication stream between separate BlackHark components can be encrypted using BlackHark:
- TLS protocol is supported for all connections between different BlackHark components (including the BlackHark server, proxies, agents, and command-line tools).
- support for pre-shared key encryption and certificates.
- For each component, encryption is an optional and adjustable feature.
- For added security, all sensitive data is encrypted and can be kept in an external vault.
- Depending on your security policy, pick an encryption algorithm from a list that is supported.
Flexible Permission
Restrict Access With a Flexible Permission Schema
![]()
BlackHark provides a flexible user permission schema which can be efficiently used to manage user permissions within one BlackHark installation or in a distributed environment. You can define three levels of permissions:
- Read-write – A Read-write Access
- Read-only – A Read-only Access
- Deny – Access Denied
User Types Are Used to Define Access to Administrative Functions and to Specify Default Permissions:
- BlackHark User have read-only permissions on collected data and events.
- BlackHark Admins can manage your monitoring configuration and read the collected data and events.
- BlackHark Super Admins are capable of managing BlackHark instance. configuration, in addition to having BlackHark Admin privileges.
User Roles
Utilize User Roles to Secure Your Process
![]()
With a detailed set of rights for various user types in your environment, create your own unique user roles. In order to meet the needs of your users and clients, user roles also provide you the ability to hide or reveal BlackHark UI elements. User Roles allow you to:
- Restricting Access to Certain UI Elements
- Limit the Ability to Carry Out Certain UI Activities
- Make a List of Allowable and Prohibited API Methods.

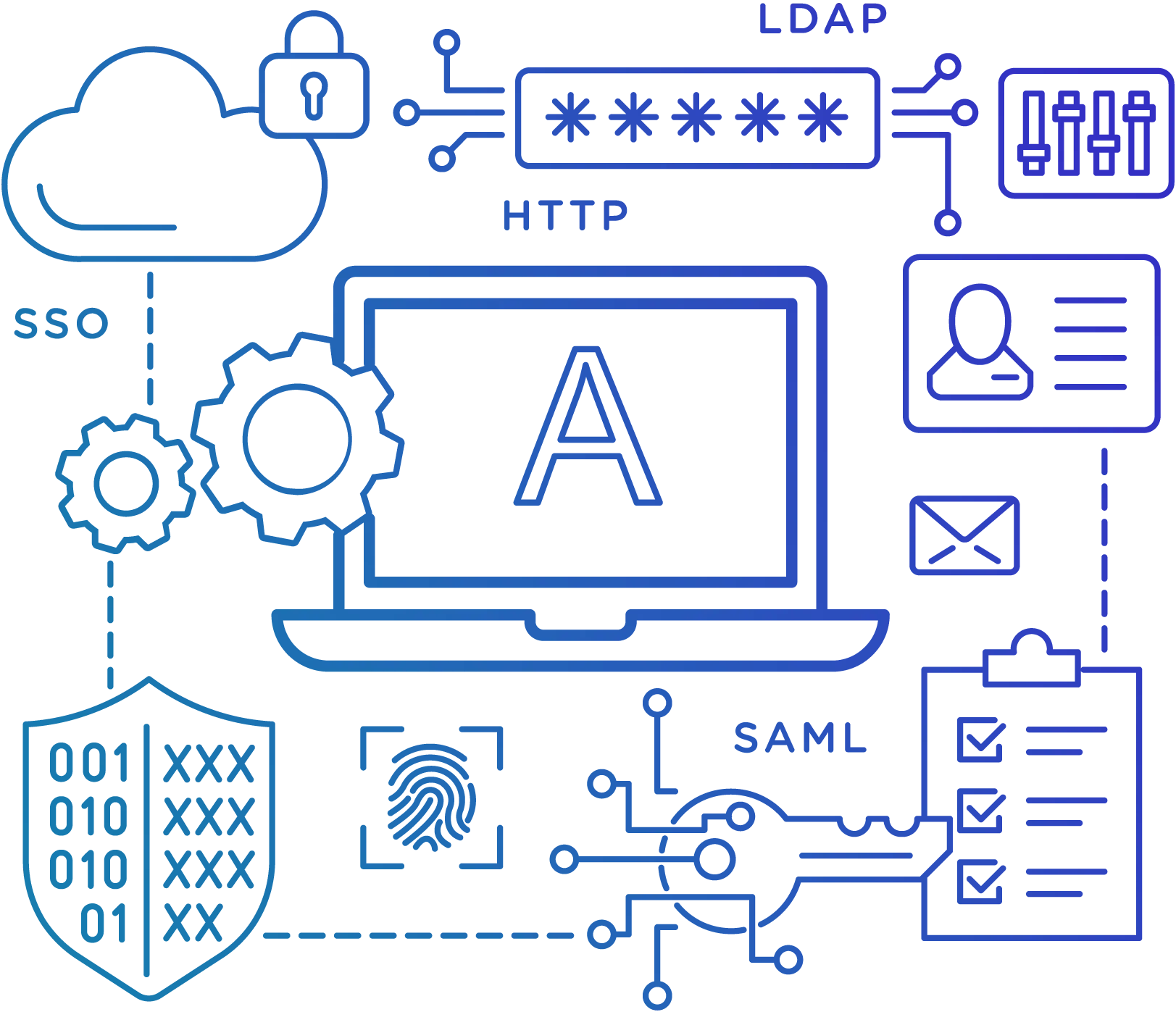
User Authentication
Using the Infrastructure That Already Exists, Authenticate Users
![]()
Connect BlackHark to your current authentication procedures. BlackHark accepts a number of authentication techniques, including:
- BlackHark Internal Logins
- Authentication Over HTTP
- Multi-factor Authentication is Supported
- Set Your Own Password Difficulty Standards
- LDAP Identification
- SAML Identification
- Authentication Using a Single Sign-on
- Native Active Directory Integration
Secret Vault
Protect Your Secrets
![]()
Once you've logged in, you can choose to shield your private data from prying eyes:
- Authentication keys, passwords, and other critical information should be kept secret.
- API or configuration export cannot be used to recover hidden information.
Install an external vault to tightly manage the access to your secrets:
- One Place to Store All of Your Secrets
- Strict Restrictions on Who Can Access the Vault
- Detailed Audit Log at the Vault Level
- Keep Your Secrets Safe in the BlackHark Vault

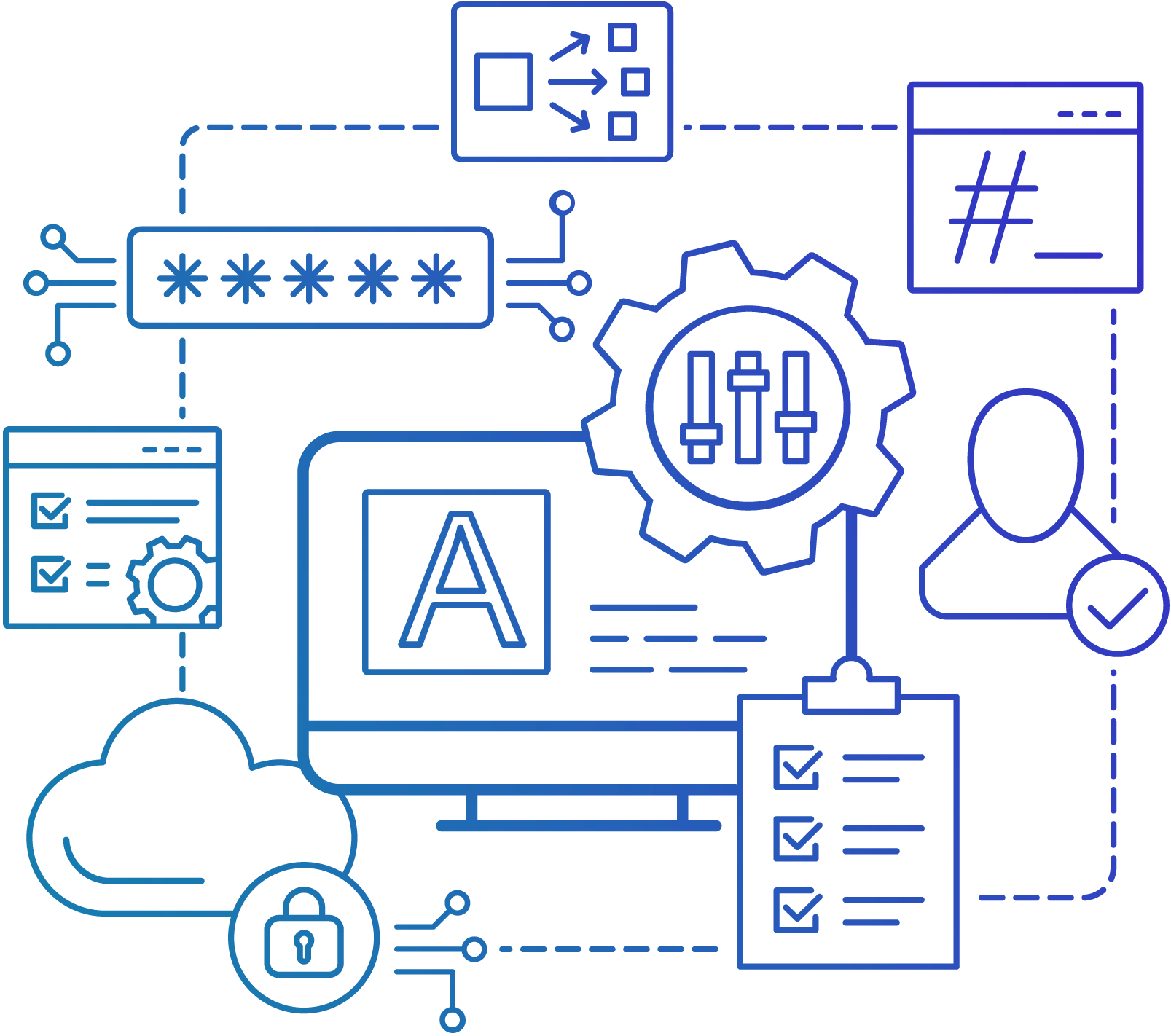
Configuration Changes Tracking
Observe Alterations to the Configuration
![]()
Utilize the Audit log to keep track of changes in your environment:
- Identify the user who modified any BlackHark entities.
- Keeps track of the IP address the user used to access BlackHark.
- Use the API to export the complete or filtered audit log for additional analysis.
- Follow changes made by a certain user to a specific resource by filtering the audit log.
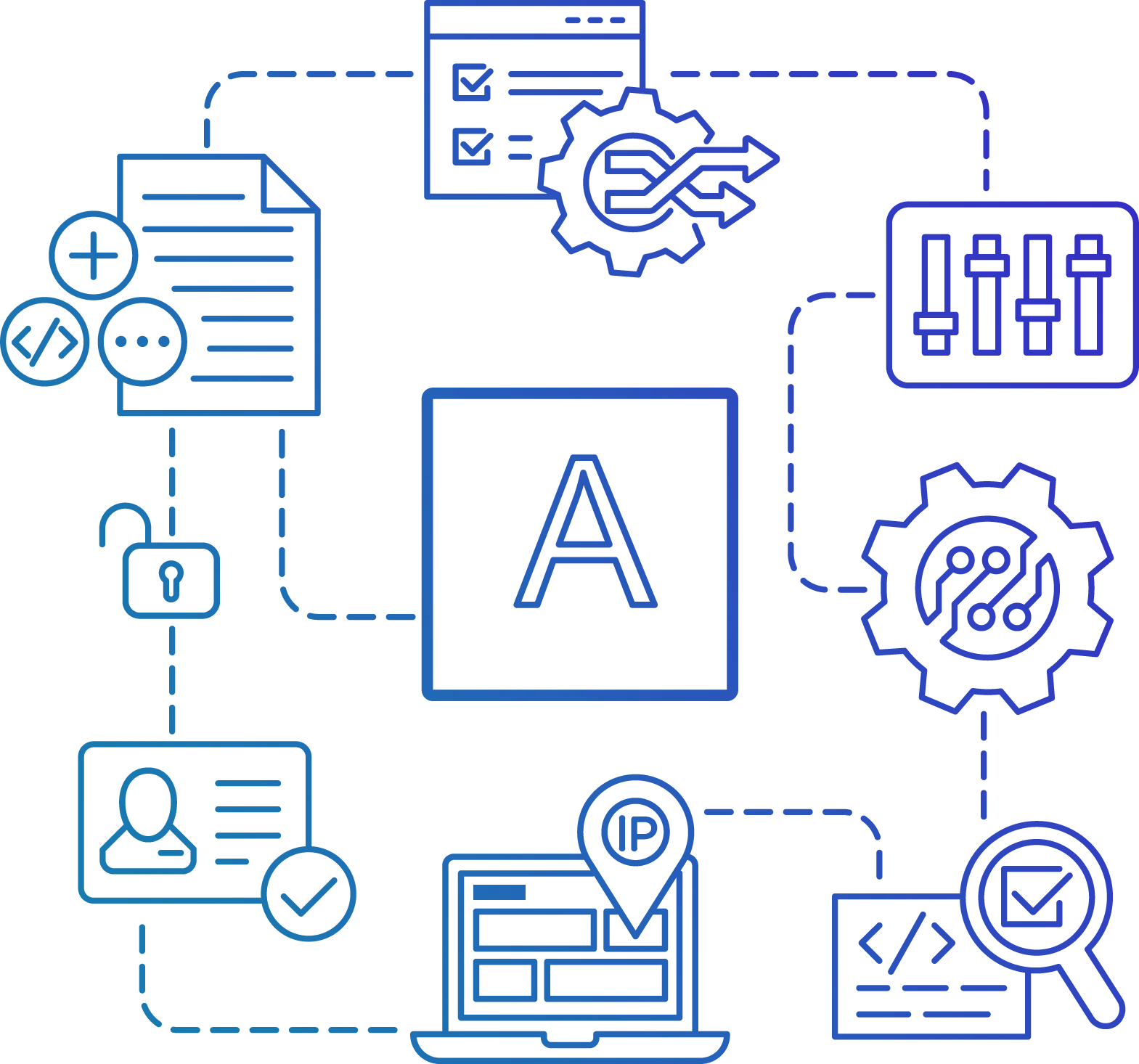
Restrict Data Collection
Limit the Acquisition of Data
![]()
Limiting the metrics that can be gathered in your environment will help you restrict access to sensitive information:
- Lists of metrics to allow and prohibit.
- Only allow connections to and from the designated endpoints.
- Limit unsecured connections to the targets of your monitoring.
- Prevent unauthorized access to sensitive information Limit network communication's direction.